In 2019, South Africa had the third-highest number of cybercrime victims worldwide.
This translates to 577 malware attacks per hour in the country – and equalling R2.2 billion in losses to South Africans every year. Experts agree that a business falling victim to one of these attacks is no longer a question of “if” but “when.”
After all, your employees are connected to the Internet all day every day. They’re communicating with colleagues and clients, sharing critical information, transacting on internet banking, downloading files and attachments, and jumping from website to website.
Today’s cyber threats don’t discriminate; businesses of all sizes are susceptible to attacks. However, small to medium-sized businesses (SMBs) in South Africa are often less prepared to deal with security threats than their larger counterparts. The reasons for this vary from business to business, but ultimately it comes down to the fact that SMBs often have fewer resources to devote to cybersecurity efforts.
In this article, we cover practical advice and tips for training employees on cybersecurity best practices with real-world examples. Prepare your employees now, before it’s too late.
Why Do Your Employees Need Cybersecurity Training?
According to over 1,700 IT service providers, the lack of cybersecurity awareness amongst employees is a leading cause of a successful ransomware attack against an SMB.
That being said, employee training is a top component of a successful cybersecurity protection program and likely the only way to ensure all staff understands the threats out there.
At the root of most attacks is the tactic of social engineering, which involves hackers manipulating a person or a company to access corporate systems and private information. Social engineering plays into the natural human inclination of trust; For cybercriminals, it is the easiest method for obtaining access to a private corporate system.
Why would hackers spend time trying to guess a password when they can simply ask your employees for it themselves?
Employee training is thus an obvious component of a successful cybersecurity protection program. Experience shows it to be an effective way to ensure all staff understands the cyber threats they face and, most importantly, what they should look for to avoid falling victim.
The Four Social Engineering Scams Your Employees Should Know About
With the above in mind, let’s help your employees help themselves.
Below is a quick and dirty overview of today’s most common and effective social engineering scams. This is the list to hand employees on their first day at work. If they don’t know these common hacker tactics, they WILL fall for them.
(1) Phishing
A 2019 study by the South African Banking Risk Information Centre (SABRIC) revealed that phishing is the most effective way fraudsters in South Africa obtain banking login credentials.
Phishing is the leading tactic leveraged by today’s malicious actors, typically delivered in the form of an email designed to impersonate a real system and/or organization.
Often crafted to deliver a sense of urgency and importance, the message within these emails often appears to be from a bank, government entity like SARS, or a popular service provider such as Telkom, and usually includes logos and branding.
These bogus platforms are designed to trick your employees into giving up sensitive information such as usernames, passwords, and business credit card and tax details.
Related:
Africa records two million phishing attacks in second quarter of 2020, Kaspersky reports
(2) Baiting
Baiting involves offering something enticing to an end-user in the unknowing exchange of private business data.
The “bait” comes in many forms, both digital, such as free torrented software, and physical, such as a USB stick labelled “Executive Salary Summary 2020” that is left in public for an employee to find. Once the bait is taken, malicious software is delivered directly into the victim’s computer. From there, it spreads to the rest of your business network resulting in a data breach.
(3) Quid Pro Quo
Similar to baiting, quid pro quo involves a request for the exchange of private data but for a service instead. In recent years, quid pro quo attacks have infamously taken the form of technical support scams. For example, your employee might receive a phone call from a hacker posing as Microsoft offering free IT assistance in exchange for login credentials.
“Scammers may call you directly on your phone and pretend to be representatives of a software company… They can then ask you to install applications that give them remote access to your device. Using remote access, these experienced scammers can misrepresent normal system output as signs of problems.
“At best the scammers are trying to get you to pay them to “fix” a non-existent problem with your device or software.
At worst they’re trying to steal your personal or financial information; and if you allow them to remote into your computer to perform this “fix” they will often install malware, ransomware, or other unwanted programs that can steal your information or damage your data or device.”
(4) Pretexting
Pretexting is when a hacker creates a false sense of trust between themselves and the end user by impersonating a client, supplier, co-worker, or even a figure of authority within the company itself. They then use this position of trust to request access to your valuable business data.
We detail a pretexting attack involving hacked mailboxes in the following article:
How an Insecure Mailbox Can Cost You R100k
Common Red Flags: Learn How to Spot a Cyber Scam
Inbox Scams
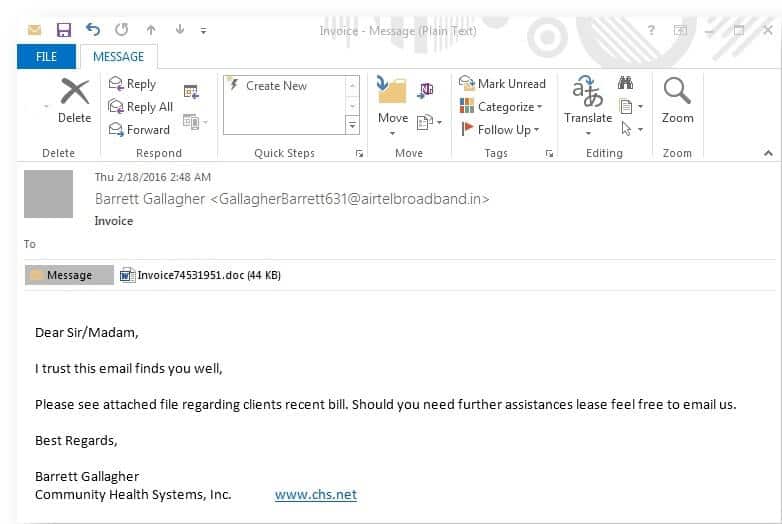
The above is a prime example of a phishing email that was used to spread Locky, a common strain of ransomware. To the recipient, the email appears to come from a supplier asking the employee to see the attached file by clicking on the attached Microsoft Word document. Note how harmless this email appears and how easy it would be for a user to absentmindedly open and click – an action that would result in an instant ransomware infection.
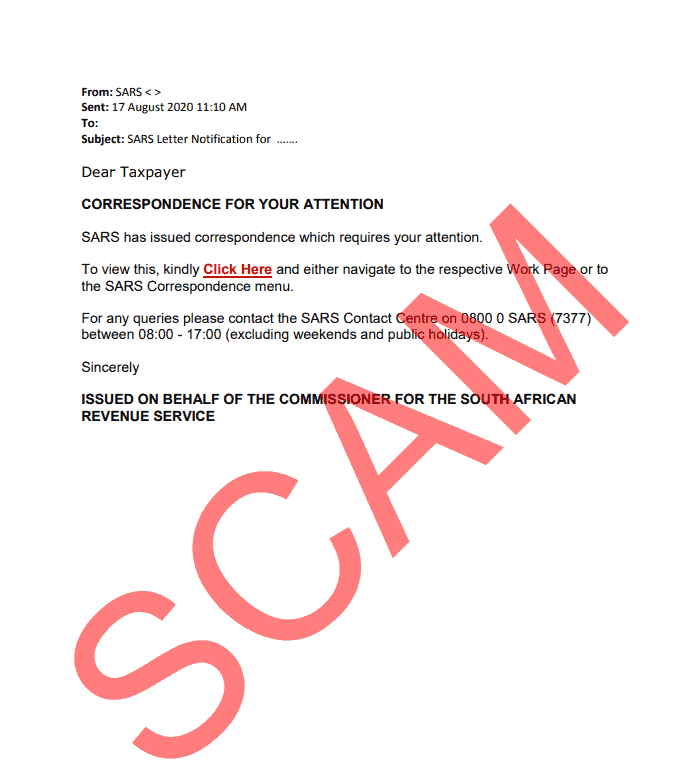
In 2020, this phishing email was used by financial scammers pretending to be from the South African Revenue Service (SARS). When clicking the link, users will be directed to a fake SARS website and prompted to enter their company SARS login details, which the scammers will then receive. View more examples of recent phishing attacks that impersonate SARS.
Red flags: Missing or mismatched sender information, generic greetings, missing or generic email signature, misspelled email addresses (For example, ‘billing@nedbannk.co.za), spelling and grammatical errors, and email addresses that don’t match their company name.
Any emails that ask the recipient to download a form or macro to complete a task are highly suspicious and an employee should NOT click on anything. Instead, report the email to IT immediately.
Malicious Websites and Popups
Malicious websites are designed to look like a page or advert on a legitimate website. These can look incredibly real by mimicking design, branding, and logos.
Typically, scammers will send links to their bogus site via email, SMS, or social media in a phishing-style attempt. Alternatively, hackers will insert code into a legitimate website which then places adverts or redirects unsuspecting users to their malicious site.
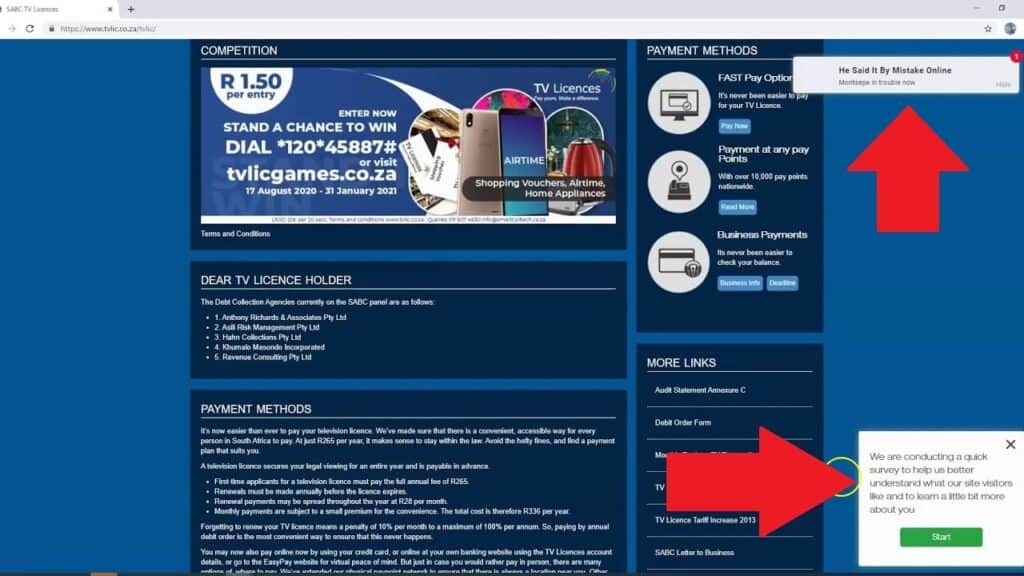
This is what happened to the SABC’s TV Licence website in December 2020. Hackers got into the website and injected code that redirected users to sites requesting personal details for bogus competitions. At times, sensationalised adverts with malicious redirects also appeared.
Popups
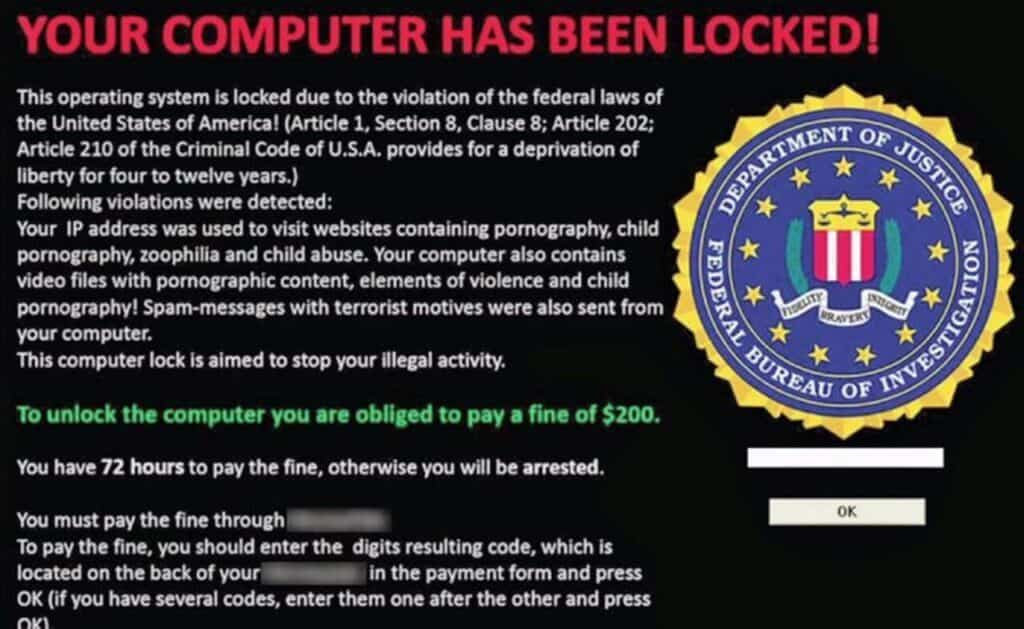
Another common lure is a pop-up that claims that a user’s computer has been locked by the FBI because it was used to access illegal material such as pirated movies or child pornography, as in the example above.
The lure instructs users to click a link to pay a fine, which is bogus. The fine is usually in a cryptocurrency, such as Bitcoin or Ethereum.
Red flags: Visiting the website automatically launches or requests a download, links that redirect to a different domain, spelling and grammatical errors, broken layout and missing images, misspelled URLs, and URLs with unusual domain extensions.
Setting Up a Cybersecurity Training Program
It is important to have a formalized plan in place to keep security front of mind and employees informed about new threats as they emerge.
Because cybersecurity threats are constantly evolving, an ongoing training schedule should be implemented companywide This should include examples of threats, as well as instruction on fundamental security best practices.
For example, teach your employees to never use the same password on multiple websites.
The frequency and intensity of cybersecurity training will be dictated by the specific nature of your business and the systems, software, and hardware you leverage. However, a good start would be ensuring that new employees receive training as part of their orientation and all employees receive training on a bi-annual basis.
Likewise, IT should work with HR to create documented and enforceable cybersecurity policies. Write and distribute a clear set of rules and instructions on cybersecurity best practices for employees. This will vary from business to business but may include policies on social media use, personal use of company devices, Two Factor Authentication requirements, password management, managing backups, web browsing, downloading torrents, and so on.
Related:
Cybersecurity Policy – Why Your Business Should Have One
Informal training can be very effective, too. Point staffers to blogs on security topics, ask them to take an online cybersecurity quiz, print out and post IT security awareness posters around the office, share relevant memes, etc.
In short, do whatever it takes to keep your employees educated and following best practices.
Get A Free Audit of Your Cybersecurity
Need to do something for your company’s cybersecurity but not sure where to start?
Whether you need guidance on developing a cybersecurity awareness program or a thorough security implementation, iSite Computers is here to help. We’ve been in the business since 2008, helping SMBs in South Africa with a fully managed IT offering and comprehensive cybersecurity solutions.
To get started, contact us today for a free consult on your cybersecurity environment. Give us a call on 031 812 9650. Or schedule a free consultation and we’ll call you back.





0 Comments